Create a Bootable USB Flash Drive Without Any App
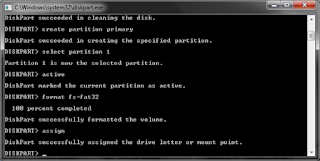
You can create a bootable USB flash drive to use to deploy Windows Server Essentials . The first step is to prepare the USB flash drive by using DiskPart, which is a command-line utility. For information about DiskPart, see DiskPart Command-Line Options . For additional scenarios in which you may want to create or use a bootable USB flash drive, see the following topics: Restore a full system from an existing client computer backup Restore or repair your server running Windows Server Essentials To create a bootable USB flash drive Insert a USB flash drive into a running computer. Open a Command Prompt window as an administrator. Type diskpart . In the new command line window that opens, to determine the USB flash drive number or drive letter, at the command prompt, type list disk , and then click ENTER. The list disk command displays all the disks on the computer. Note the drive number or drive letter of the USB flash drive. At the c...




